Password-less login from managed devices
The following describes the configuration in Ivanti Access for Zero Sign-on.
Deploying Authenticate using UEM
You can connect UEM with Ivanti Access and distribute Authenticate to user desktops.
Procedure
-
In Ivanti Access, go to Profile > Zero Sign-on.
-
Under Steps for deploy, expand Deploy Authenticate using UEM.

-
For desktops managed by :
-
3rd Party UEM: In Ivanti Access, go to UEM > 3rd Party UEMstab. Click Connect UEM and follow steps.
-
Ivanti Neurons for MDM: Go to UEM. Select the Ivanti Neurons for MDM UEM and follow steps in the Authenticate section.
Review Registration Settings
The Registration settings are used by clients such as Go to register user’s device with Ivanti Access.
Procedure
-
In Ivanti Access, go to Profile > Zero Sign-on.
-
Under Steps to deploy, expand Review Registration Settings.
Verify the certificate mapping.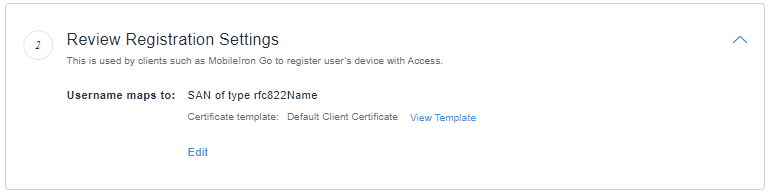
-
Click View Template to view the default client certificate.
-
Click Edit to modify the registration.
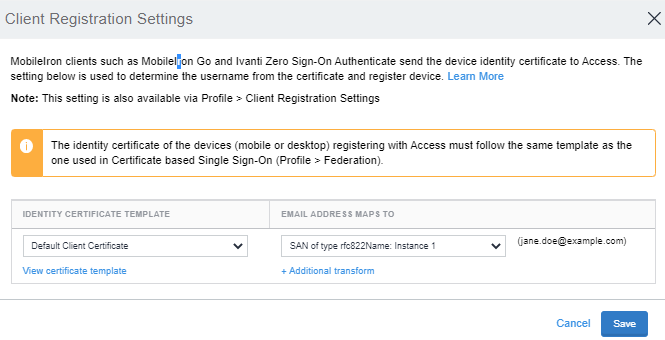
-
Select the username mapping in the certificate appropriately and click Save. For more information, see Client Registration Settings.
For information about MiTra expressions, see Language to generate values from certificate fields.
Enabling Password-less Authentication on Go and Mobile@Work
Before you begin
-
Configure the user information for Zero Sign-on.
-
To configure the user information, map the fields in the certificate from which Access gets user identifying information. This is the identity certificate used for setting up configuration. Configuring the user information enables passwordless authentication.
-
Procedure
- In Ivanti Access, go to Profile > Zero Sign-on.
- Under Steps to deploy, expand Enable Password-less Authentication on Go and Mobile@Work.
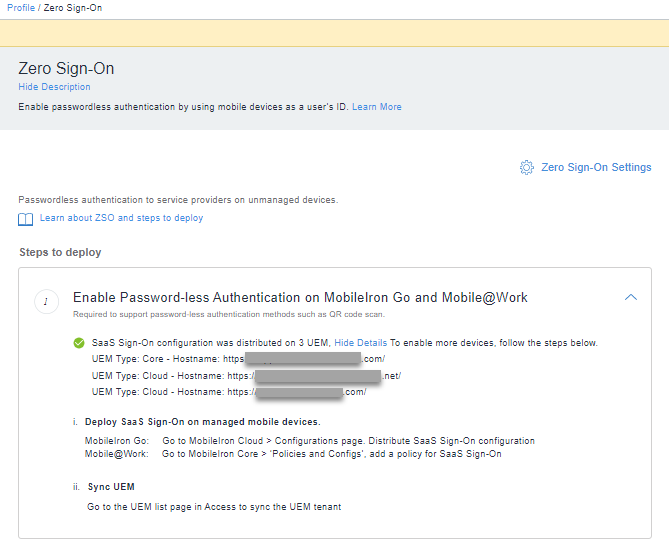
- Click See Details to view the existing configuration details for the devices.
- To enable more devices follow the steps i) and ii) as shown above.
- Deploy SaaS Sign-On on managed mobile devices.
-
Sync UEM.
Adding a Zero Sign-on Rule in the Policies
In the policy associated with the saml pair for which Zero Sign-on is required, add a Zero Sign-on Rule conditional rule. If the rule is added, users accessing the cloud service from an unmanaged device see an interaction page. The interaction page contains a QR code, which device users can scan from a managed device to authenticate to the cloud service. Alternately, the interaction page also contains a link to authenticate with username and password.
Before you begin
- Ensure that mobile app single sign-on is configured for the federated pair or delegated IdP to which you want to assign the Zero Sign-on Rule. If mobile app single sign-on is not configured, you will see errors when creating or assigning the Zero Sign-on Rule.
Procedure
- In Ivanti Access, go to Profile > Zero Sign-on.
- Under Steps to deploy, expand Add Zero Sign-On Rule in the Policies.
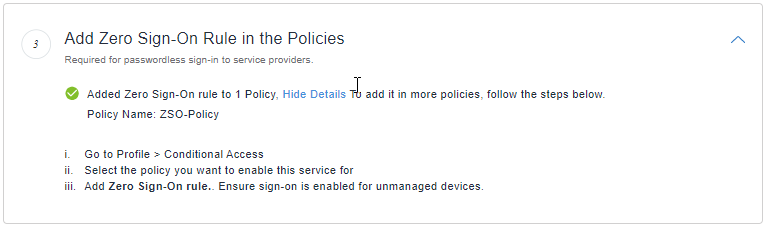
- Verify that the rule is configured.
Else add a rule in Profile > Conditional Policies. - In Ivanti Access, go to Profile > Conditional Access.
- Expand Default Policy.
If you want Zero Sign-on only for some federated pairs or delegated IdP, create a new policy.
The Zero Sign-on rule can be added to any policy. Adding the Zero Sign-on rule to the default policy makes it available to all pairs to which the default policy is applied. Add the Zero Sign-on rule to another policy if you want to apply the rule to only some federated pairs or delegated IdP. -
Click +Add Rule > Zero Sign-on Rule to add the conditional rule for Zero Sign-on.
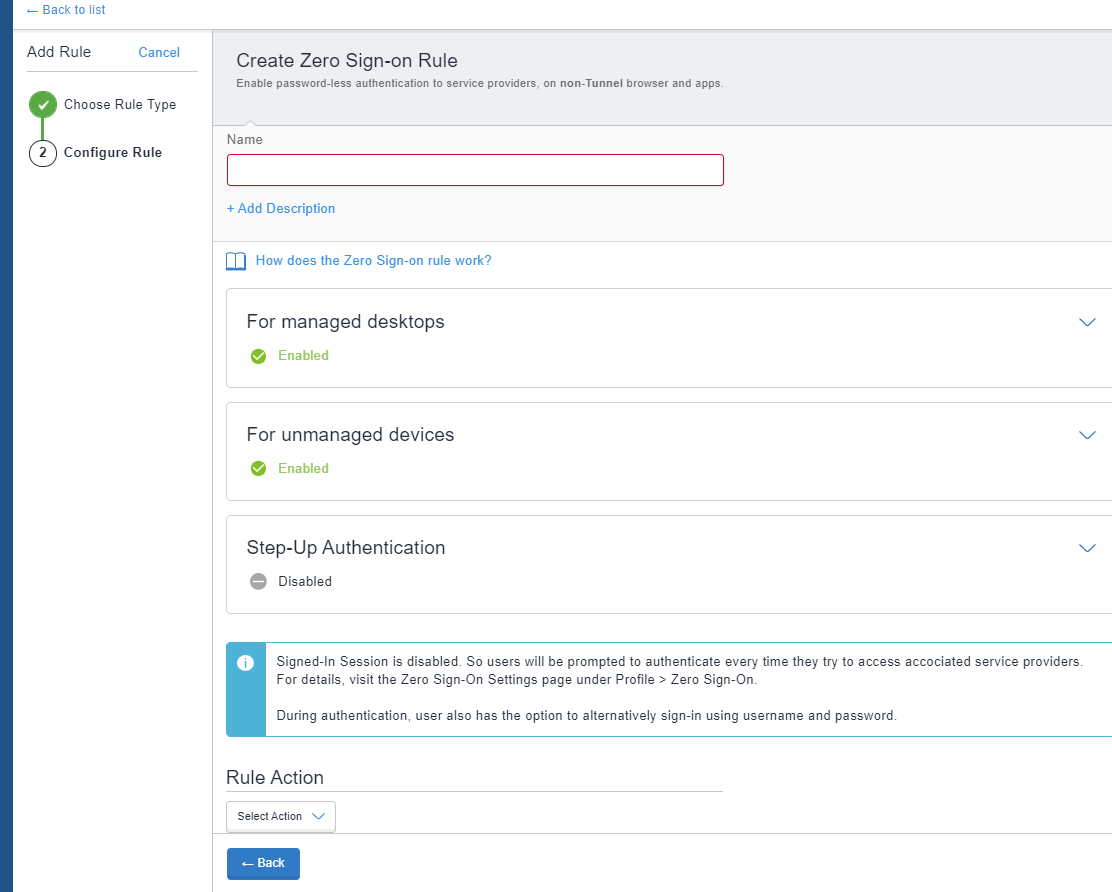
- Enter a Name and Description for the rule.
- Configure the rule for one of the following devices.
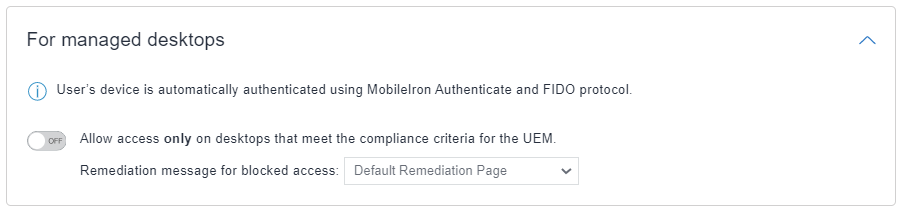
- For managed desktops: Users device is automatically authenticated using Authenticate and FIDO2 protocol. Enable the toggle switch to select this configuration.
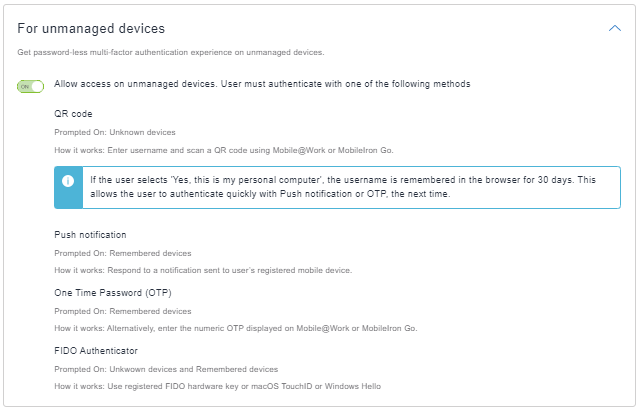
- For unmanaged devices: Enable the toggle switch to allow access on unmanaged devices. Users are authenticated with one of the following methods: QR code, Push notification, One Time Password (OTP), and FIDO Authenticator.
- Step-Up Authentication: Enable the toggle switch to step-up authentication such as Push notifications or biometric for managed desktops.
- For managed desktops: Users device is automatically authenticated using Authenticate and FIDO2 protocol. Enable the toggle switch to select this configuration.
- For Rule Action, select Allow.
- Click Done to save the policy and rule.
: The order of the conditional rules matters. When you create a Zero Sign-on Rule, Ivanti Access automatically orders the rules such that the Zero Sign-on Rule follows the Trusted App and Device rule. The order of rules, if they are configured, is as follows: Trusted App and Device rule, Zero Sign-on Rule, Multi-Factor Authentication rule. However, the rules can be manually reordered. Ensure that the order of the rules matches the order stated in this note.
Configuring branding for Zero Sign-on
Customize the user experience for your enterprise users by uploading your company logo to Ivanti Access. The user notification screen as well as the interaction page with the QR code are customized to display your company logo.
Ensure that your company logo is no more than 260 pixels wide by 30 pixels high. Supported file types are: PNG, JPG, JPEG, and SVG.
Procedure
- In Ivanti Access, go to Profile > Branding.
- In the Company Logo section, drag and drop your company logo or click Choose to navigate to the location of the file and add.
Next steps
Publish the updates. See Publishing the changes.
Publishing the changes
Publish the changes to make the updates available. In the Ivanti Access administrative portal, a publish banner appears in any of the Profile tabs when there are configuration changes.
Procedure
- In Ivanti Access, go to Profile > Overview.
- Click Publish.
- Click OK.